Stix is a messaging app created for activists, journalists, and anyone seeking a secure, simple, and reliable way to communicate. Unlike conventional messaging apps, Stix operates without a central server—messages are synchronized directly between users’ devices. If the internet is unavailable, Stix can sync through Bluetooth, Wi-Fi, or memory cards, ensuring information continues to flow during a crisis. When the internet is accessible, Stix syncs via the Tor network, safeguarding users and their connections from surveillance.
The quick start guide and the manual explain how to use Stix and detail the features it offers.
Stix utilizes direct, encrypted connections between users to prevent surveillance and censorship.
Traditional messaging software depends on central servers, making messages and relationships vulnerable to surveillance.
Stix can share data through Wi-Fi, Bluetooth, and the Internet.
Stix offers private messaging, public forums, and blogs that are safeguarded against the following surveillance and censorship threats:
- Metadata surveillance. Stix uses the Tor network to prevent eavesdroppers from discovering which users are communicating with each other. Each user’s contact list is encrypted and stored on their own device.
- Content surveillance. All communication between devices is encrypted end-to-end, protecting the content from being intercepted or altered.
- Content filtering. Stix’s end-to-end encryption blocks keyword filtering, and its decentralized design ensures there are no servers to block.
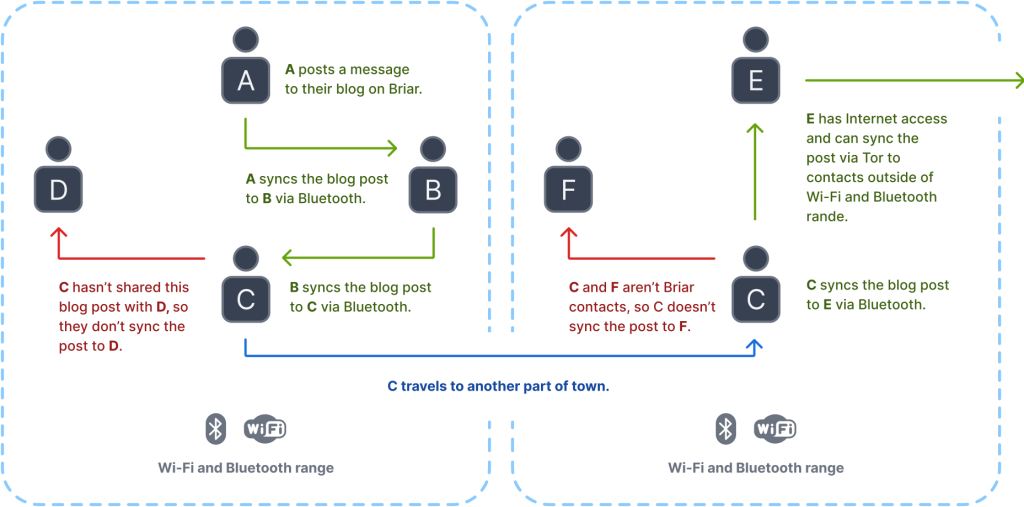
- Takedown orders. Every user subscribed to a forum retains a copy of its content, eliminating any single point where a post can be removed.
- Denial of service attacks. Stix forums operate without a central server, and every subscriber retains access to the content even when offline.
- Internet blackouts. Stix can function over Bluetooth and Wi-Fi, maintaining the flow of information during outages.
Stix is designed to resist surveillance and censorship by an adversary with the following capabilities:
- All long-range communication channels (internet, phone networks, etc.) are fully monitored by the adversary.
- The adversary can block, delay, replay, and modify traffic on long-range communication channels.
- The adversary has limited capability to monitor short-range communication channels (Bluetooth, Wi-Fi, etc.).
- The adversary has limited ability to block, delay, replay, and modify traffic on short-range communication channels.
- The adversary can deploy an unlimited number of devices running Stix.
- Some users can keep their devices secure—those who can’t are treated, for the purposes of this threat model, as being under the adversary’s control.
- The adversary has limited capacity to persuade users to trust its agents, restricting the number of social connections between the adversary’s agents and the rest of the network.
Our long-term vision extends well beyond messaging: we aim to leverage Stix’s data synchronization capabilities to support secure, distributed applications like crisis mapping and collaborative document editing. Our ultimate goal is to empower people in any country to create safe spaces for open debate, event planning, and organizing social movements.